 You know how you’re told to put your private social security number or credit card information only into sites that are secure? Their site address is https:// instead of just http:// . Your browser will display a lock icon, turn something green, or give you another indication that what you send in cannot be stolen by third parties?
You know how you’re told to put your private social security number or credit card information only into sites that are secure? Their site address is https:// instead of just http:// . Your browser will display a lock icon, turn something green, or give you another indication that what you send in cannot be stolen by third parties?
Well, it turns out these https:// sites are not secure at all.
Monday one of the biggest suppliers of encryption code said that their widely used library has a flaw in it which allows anyone to look at 64,000 characters that is in the host server’s memory. Your retirement account username and password and social security number might be part of the 64kB of information a passing bad guy looked at. Or, the username and password to Gmail account could have been scraped and sent to Bad Guy Central.
And, the theft of your information would leave no trace on the victimized computer server at Wells Fargo, Bank of America, Chase, or wherever.
The Ugly
This bug has been named “Heartbleed” in a nerdy reference to the communications heartbeat code that it lives in. Cute name, but I’ve seen statements that the seriousness of Heartbleed on a scale of 1 to 10 is 11.
The geek world is uniformly saying that this problem is very awful.
On the Other Hand
I cannot find a report from anyone anywhere that says this bug is the apparent source of any loss of data, money, or privacy. The bug was discovered by honest programmers who notified the people responsible for the faulty code. A patch was immediately released, and most larger sites have already updated their servers.
2 Actions You Must Take!
Still, the Heartbleed problem is real, and there is a potential that some bad guys have broken into systems and have used, or have stored for future use, the information they stole. They could have broken into your bank just as you logged on, which would give them your username and password. They could have done the same with your investment firm, credit card company, or many other places you enter data you want to keep private and secure.
So, you need to change your passwords for every secure site. Today.
I suggest using LastPass for creating strong new passwords and tracking them. (See this post for more information on why.) But, whether your use LastPass or manage your passwords manually, at the very least add or change one character for all of your current passwords.
But, first, make sure that your secure service has patched its software. If not, change the password now, do not use the site for secure transactions, and check again tomorrow. Now that the bug is well known and easy to exploit, your chances of having your data stolen on an unpatched server is much, much greater than it was last week.
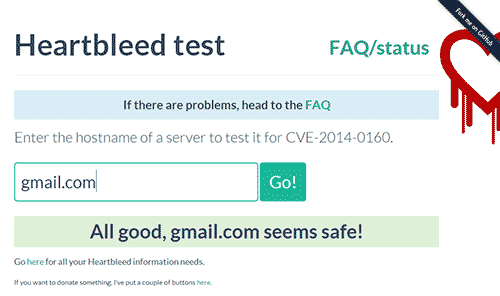
C/net recommends http://filippo.io/Heartbleed as a place to test whether the Heartbleed patch has been installed. Use it!
References To Read
Here are sites I used for this post. Check them out for more information.

Leave A Comment